Trusting NESS with your SENSITIVE Data!
NESS is a division of Nexus Eurotech a global technology company based in Estonia.
We have been operating in the FinTech industries for more than three decades now.
The robustness and scalability of our systems allow for a cost effective security solution from entry level financial institutions to multinational conglomerates who are required to protect vast amounts of sensitive data.
We are pleased to announce that our fault-tolerant replicating token devices have to date processed nearly half a billion financial tokens and continue to add to this number at a rate of up to 1.5 million transactions daily.
Learn why major international corporations trust our products with millions of their sensitive data elements.
Circle of Trust
Point to Point Protection At Your Fingertips
After first contact and initial security review we will focus on working with you to ensure that the solution we offer meets and exceeds your expectations for both effectiveness and cost-efficiency.
We will stop at nothing to ensure your absolute trust and confidence in our solutions. If we do not have the answer we will walk the extra mile to find it for you.
Keeping your sensitive data secure
Assets Protection
Data Protection
In the office or on the move, you are covered
Tokenization
Enhancing the protection of sensitive data with token-based data substitution
PCI Compliance
Payment Card Industry Security Standard (PCI DSS) experts with Certified Payment-Card Industry Security Auditors partnering with world class compliance partners.
We are NexTech Euro Secure Solutions (NESS)
Team Members
Core Team

David
Head of Global Business Development
Julio
International Director
Manuel
Lead Representative & Business Development
Carlos
Lead Developer & System Design
Efrain
Lead Systems Architect & IntegratorKnow More About Us
Frequently Asked Questions
- General
- Token
What is Tokenization ?
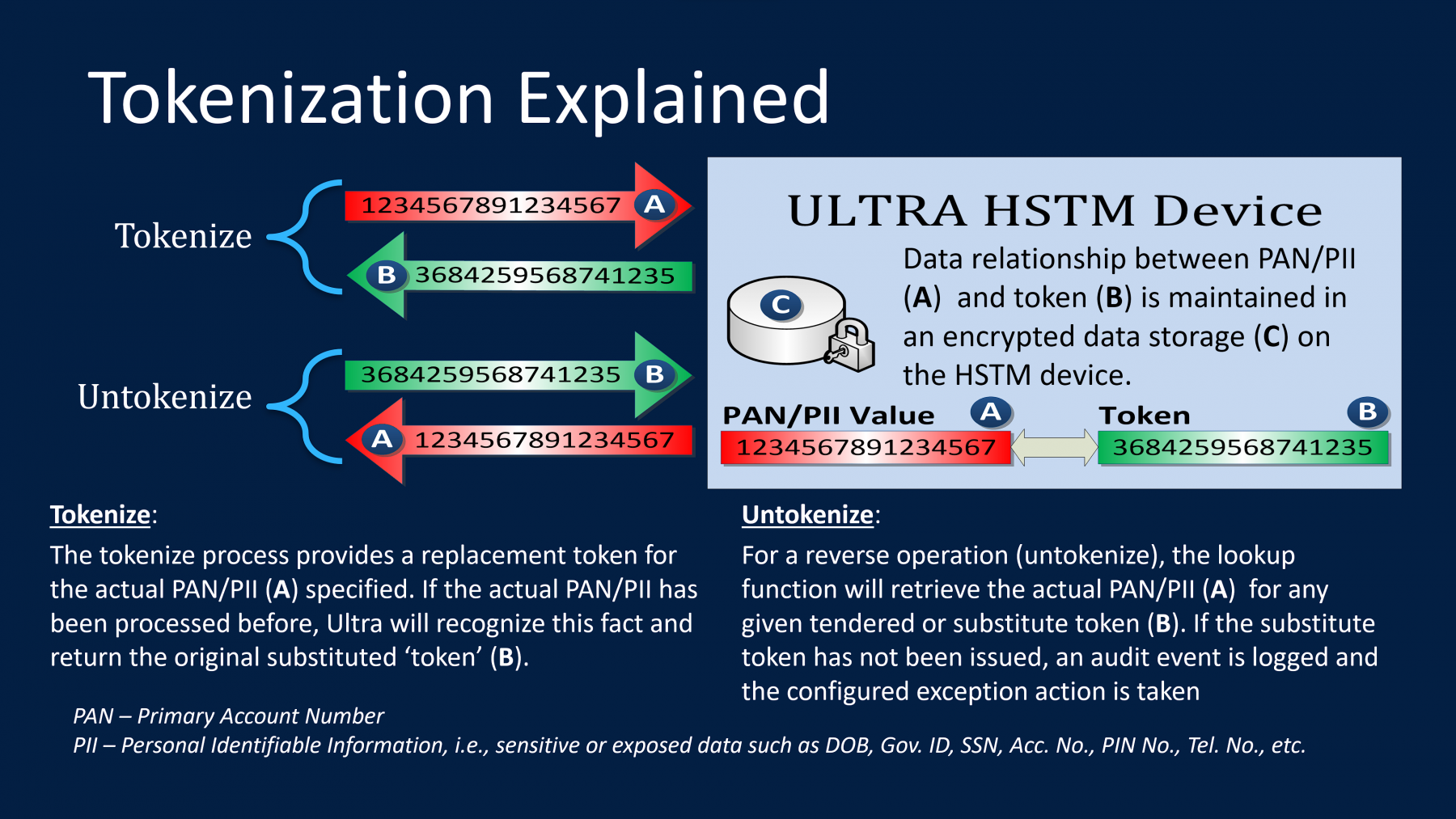
“A token is essentially an alias / surrogate or substituted data value which cannot be used to derive the original identity data”
Our ULTRA HSTM ™ solutions provides a substitute token for any given original Primary Account Number (PAN) or sensitive Personal Identifiable Information (PII) value. Within a secure closed system, the replacement token provides a reference to the original data element; which allows Ultra to retrieve the original PAN/PII for a specified token. The original and replacement elements are not related in any way mathematically or cryptographically so the original PAN/PII cannot be determined outside of the appliance from the token.
What is the ULTRA HSTM ™ Tokenization Bureau Service ?
We will not try to sell you a solution that you do not need. Our PCI Compliant Data Center offers a full Tokenization Bureau Service that allows you to solve your PCI challenges to cost effective manner.
We, together with our dedicated partners will analyze your business needs and offer a suitable and secure solution, overcoming any resource and budgetary constraints you might face.
Data Security Process Review
Let NESS do a complete security assessment to pin-point and plug any security holes you might have in your data environment you might have in your environment.
We believe prevention is better than a cure!
PCI Compliance Review
We are aware that PCI Compliance can be a challenge to most clients. NESS has a strong internal team, together with our dedicated compliance partners have many years of hands-on security experience, especially in in EFT/FinTech and Retail industries.
Why Your Organization Needs It?
All transaction history and potential PII such as names, addresses, DOB, email, payroll information and bank account numbers are kept in repositories for data mining usage which leaves them exposed to abuse. Organizations depend on such data for their customer (loyalty) tracking and analysis of spend-ing habits to manage and grow their business.
In almost every organization, such valuable information, e.g., business reports, HR documentation,
customer data and research results is saved electronically without being sufficiently protected. This PII information can, in a cumulative way, contribute towards data theft. Also, the current practice of saving data centrally on servers, multi-site workplace networking, and the use of mobile data media greatly increases security risks.
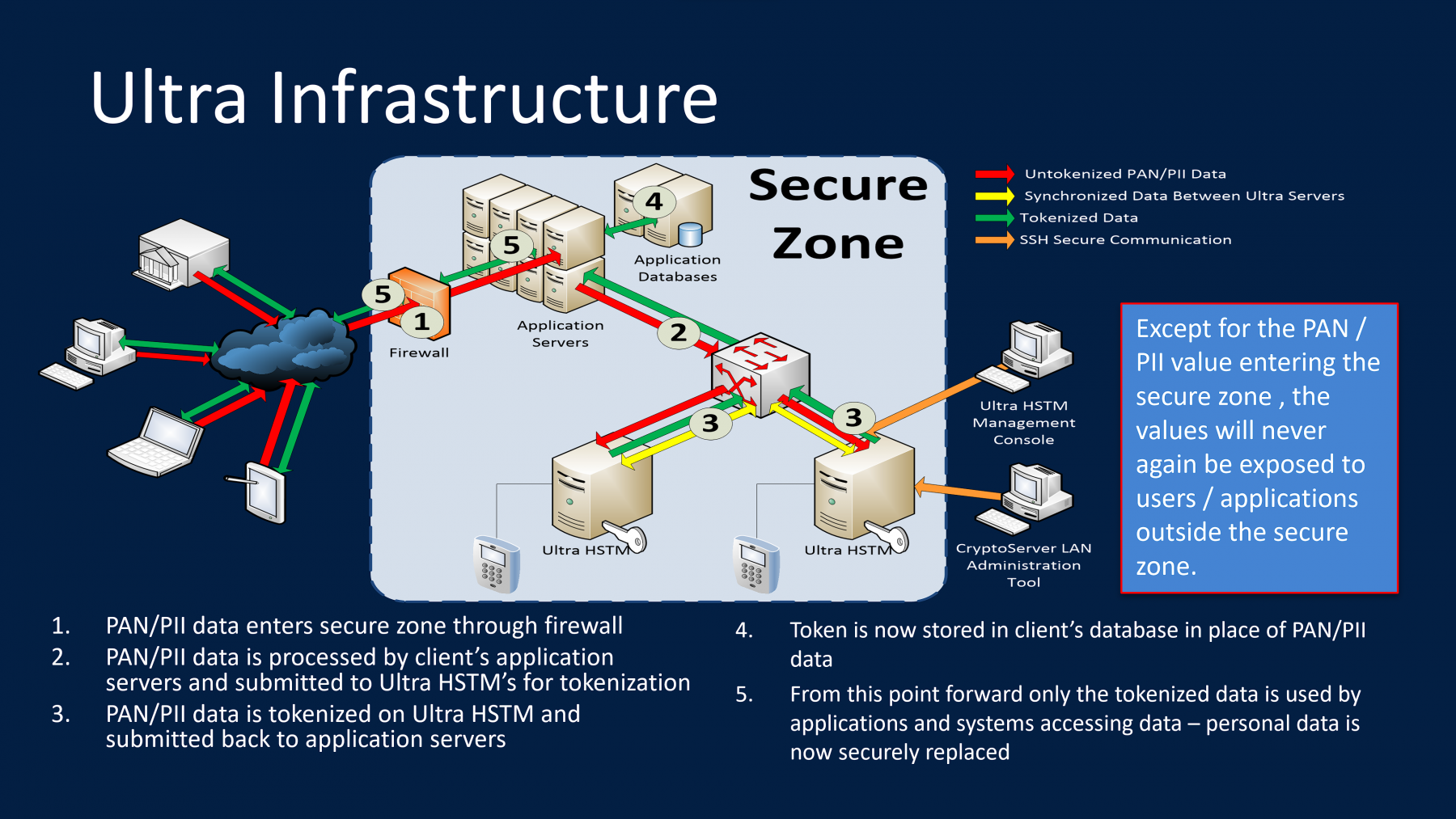
As more organizations outsource their IT departments in an effort to duce costs, they are faced with increasing data confidentiality concerns as well. What is needed is an integrated security solution that protects your data in multiple ways. The ULTRA HSTM ™ solution is unique in that it protects your data through:
-Replacing your vulnerable data with tokens which cannot be traced back to the original data value outside the ULTRA HSTM. The token can be configured in such a way that it Will Still pass business rules and be used for computing, viewing and reporting.
-Encryption of all vulnerable data on the ULTRA HSTM database using a hardware security module (HSM) protecting the data even within the secure zone of the organization.
-Data communication between the ULTRA HSTM and other systems is through the ULTRA API, which provides Secure Shell (SSH) protocol communication with application authentication.
-The HSTM is a tamper resistant device with an encapsulated HSM computing unit for enhanced secure data storage.
The Tokenize / Untokenize Process
For a reverse operation (untokenize), the lookup function Will retrieve the actual PAN/PII. for any given tendered or substituted token. If the substitute token has not been issued, an audit event is logged and the configured exception action is taken.
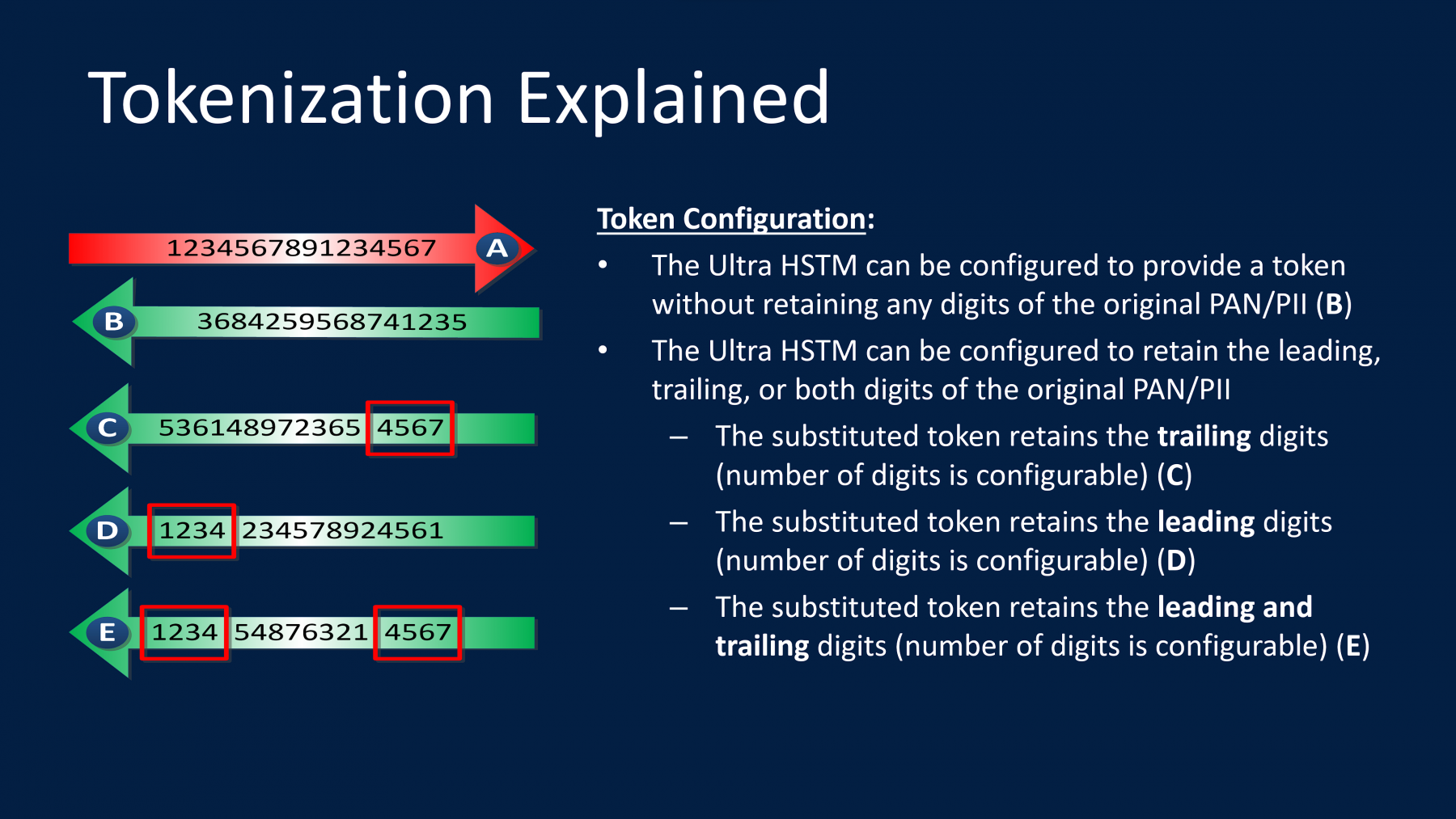
Our ULTRA HSTM ™ can be configured to provide a token in a variety of configurations, such as:
1. Without retaining any digits of the original PAN/PII.
2. Retain the leading, trailing, or both digits of the original PAN/PII.

Hosted Secure Tokenization Module
How Tokenization Works
24/7 Online Support
Dedicated Response
We will do our best to respond to your questions or request in a professional and timely manner. Existing clients should refer to response times as specified in the Service Level Agreement. If your question is of a sales nature please refer to the sales email address on this page or if you have technical related question or concern please direct the enquiry to our qualified technical support team.